LWC are custom HTML elements built using HTML and modern JavaScript (Ecma Script) and stylesheets. LWC is built over core Web Standards and Salesforce has used shadow DOM concepts for securing page data.
As LWC is built on HTML, there could be session tempering over the internet. We can use Health Checkup for finding inactive session security setting in Salesforce application. Salesforce provided many technique for securing sessions.
Let us explore top 5 session setting which can be applied for securing Salesforce application specially for LWC.
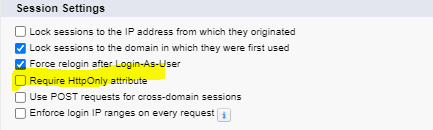
1. Require HttpOnly Attribute
An HttpOnly Cookie is a optional attribute added to a browser cookie that prevents client-side scripts from accessing data. This attribute is set by web server while sending response back to web browser.
In most of programming languages we can set this attribute like below
setcookie("sessionid", "QmFieWxvbiA1", ['httponly' => true]);In Salesforce, this can be done easily by setting up property in Session Setting Setup page.
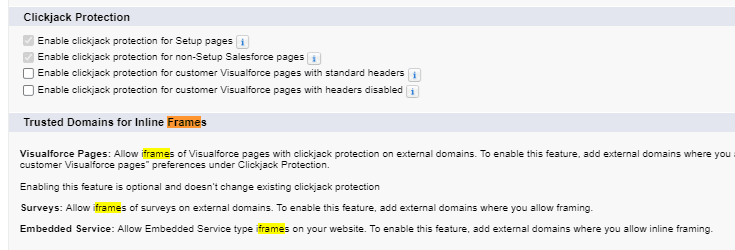
2. Enable Clickjack Protection
Clickjacking is an web attack that tricks a user into clicking a webpage element which is invisible or attached as another element. This can cause users to unintentionally download malware, provide credentials or sensitive information and visit malicious web pages.
Clickjacking is performed by displaying an invisible page or HTML element, inside an iframe, on top of the page the user sees. The user thinks they are clicking the visible page but actually they are clicking an invisible element in the additional page transposed on top of it.
This clickjacking can be protected by client side Frame Busting and server side X-Frame-Options. X-Frame-Options header indicates whether or not a browser should be allowed to render a page inside a <FRAME> or <IFRAME> tag.
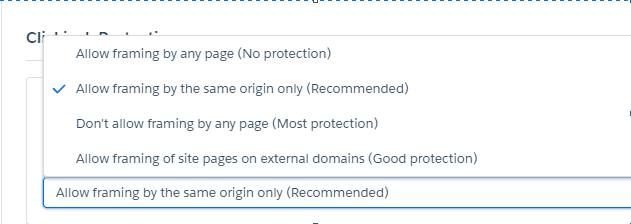
In Salesforce we can easily setup clickjack protection using Session Setting setup page.
We can also setup clickjack for community from community security setup page.
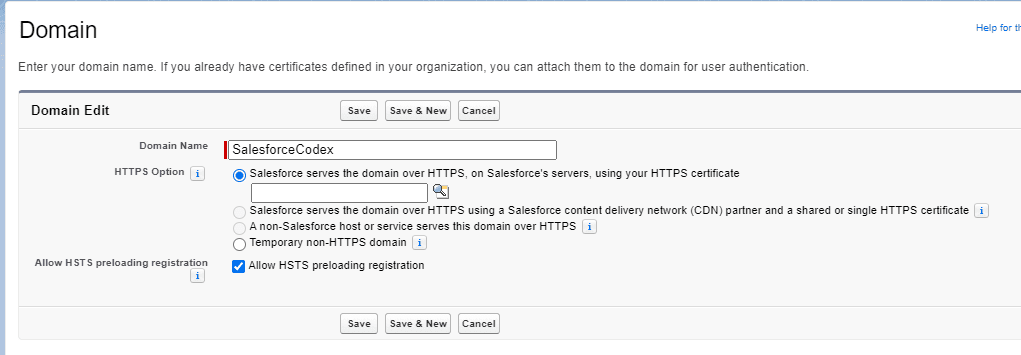
3. Require HTTPS
To safeguard data, Salesforce plans to disable HTTP-only domains by July 2021. HTTPS has Transport Layer Security (TLS) protocol, which makes it more secure than HTTP. TLS is designed to facilitate data security and privacy for communications over the internet.
Enable HTTPS on a custom domain
HTTPS should be enabled for all custom domain. For enabling HTTPS, enable proper setting while creating domain based on requirement.
4. Session Timeout
If our application is storing sensitive information, we can set shorter session timeout.
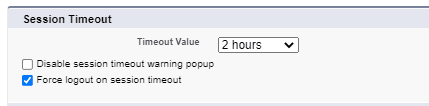
Setting which we can do are
- Timeout – Set timeout based on your requirement. Minimum timeout can be 15 min and Maximum timeout value can be 24 hrs.
- Force logout on session timeout – If this setting is enabled then system will logout when session is timed-out.
- Disable timeout warning popup – This will prompt a warning message that session will be timed-out in 30 seconds.
5. Enable Cross-Site Scripting (XSS) Protection
Cross-site scripting (XSS) is a computer security vulnerability that allows malicious attackers to inject client-side script into web pages viewed by other users. They can steal application data using this attack.
Salesforce has security setting which protect from XSS attack. If XSS attack reflected then blank page is returned so attacker can not insert any script.

Reference:
Posts for LWC DataTable Components
Search Knowledge Articles faster using Search Keyword
