Data is the biggest asset in today’s digital world. This sensitive business data should be protected from unauthorised user access. Although Salesforce offers comprehensive security features to regulate data access, there is still a possibility of large-scale data exports, whether deliberate or unintentional, which may result in data breaches or compliance issues. This is where transaction security policies are implemented.
This post will provide a step-by-step guide to implement the transaction security policy for preventing large data queries.
Check our post, Enhance Salesforce File Security with FileEvent to prevent file downloading in Salesforce using transaction security policy.
Table of Contents
- What Are Transaction Security Policies in Salesforce?
- Why Limit Large Data Exports?
- Common use cases of Transaction Security Policy
- How to Prevent Large Data Queries with Transaction Security Policies
- Method 1: Using Condition Builder (No-Code Approach)
- Method 2: Using Apex
- References
- Related Posts
- Need help with setting up a transaction security policy?
What Are Transaction Security Policies in Salesforce?
Transaction Security is a Salesforce feature that monitors activities in real time and detects potential security issues using custom criteria defined by admins. It serves as a framework for intercepting user events such as logins, report exports, and API enquiries and executing predetermined actions when certain circumstances are satisfied. These policies are based on events, which are immutable and timestamped records of Salesforce activity, like user interactions or data modifications.
A transaction security policy has three important components:
- Events are the precise activity being tracked (e.g., API Event, Report Export Event or Login Event).
- Conditions: Rules that describe when the policy should be triggered, which may be defined using a no-code Condition Builder or Apex code.
- Actions are responses to triggered conditions, such as stopping an action, sending notifications, or requesting extra authentication.
This functionality requires a Salesforce Shield or Salesforce Shield Event Monitoring add-on subscription to allow sophisticated monitoring and policy enforcement. Enhanced Transaction Security expands on this by allowing policies to be applied to real-time events, resulting in proactive control over user behaviour.
Why Limit Large Data Exports?
Large, unrestricted data exports can:
- Expose sensitive information to unauthorized access.
- Increase the risk of data leaks through downloads or emails.
- Violate compliance requirements like GDPR, HIPAA, or industry-specific regulations.
- Impact system performance, especially when massive queries are run during business hours.
By setting up transaction security policies for record count limits, you can ensure users only retrieve the amount of data necessary for their job.
Common use cases of Transaction Security Policy
- Blocking logins from untrusted locations or devices using the Login Event.
- Monitoring API queries to prevent unauthorized data pulls via the API Event.
- Restricting access to list views or reports containing sensitive data.
- Preventing large-scale data exports, which we’ll explore in detail in this post.
By implementing these policies, organizations can enhance security without disrupting legitimate user workflows.
How to Prevent Large Data Queries with Transaction Security Policies
Large data queries pose a significant risk, as they can lead to accidental or intentional data leaks. Transaction Security Policies address this by targeting the API Event (or Report Export Event for report downloads), allowing you to block API queries exceeding a certain row count. Salesforce provides two primary methods: the no-code Condition Builder for straightforward policies and Apex for more nuanced control, such as role-based restrictions.
In this post, I will use Postman to retrieve records and check how the transaction security policy will block Postman requests.
Method 1: Using Condition Builder (No-Code Approach)
Follow the steps below to set up transaction security policies using the code builder
1. To set up the transaction security policy using the condition builder, navigate to Transaction Security Policies from setup. If it’s your first time, click Enable next to “Get Started With Transaction Security”.
2. Click New, select Condition Builder, and click Next.
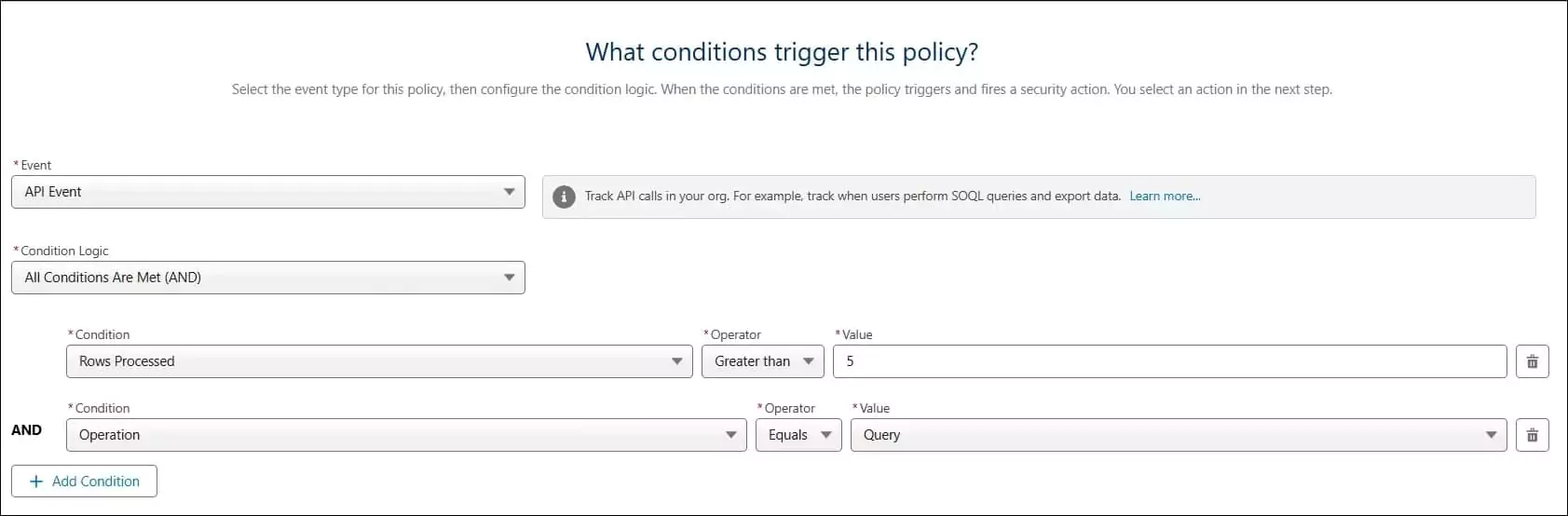
3. Add conditions to trigger the transaction security policy
- Set Event to “API Event”.
- Choose All Conditions Are Met for Condition Logic.
- Add Condition 1: Rows Processed > Greater than or equal > Enter a value (e.g., 1000). Add Condition 2: Operation > Equals > “Query”
- Click Next
4. Add what action should be taken when the policy is triggered
- Select ‘Block’ as the action.
- Select the default message in Block Message. If you want to change text, then select Custom Block Message
- Select the Notification type, like email notification or in-app notification. Select user for notification. It can be an admin user.
- Select Email Notification Content, like what message needs to be sent
5. Put the transaction policy name and description
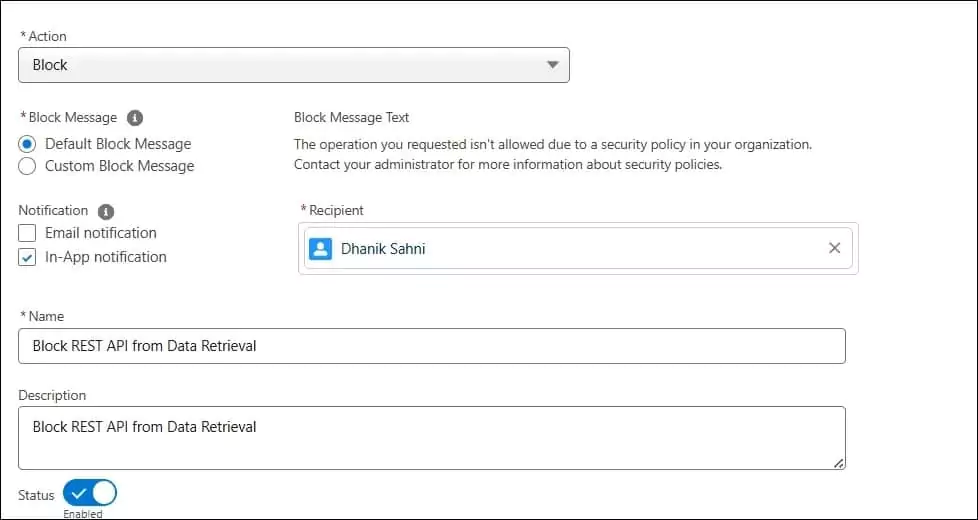
6. Enable the created transaction policy by toggling Status to enabled on the Actions tab.
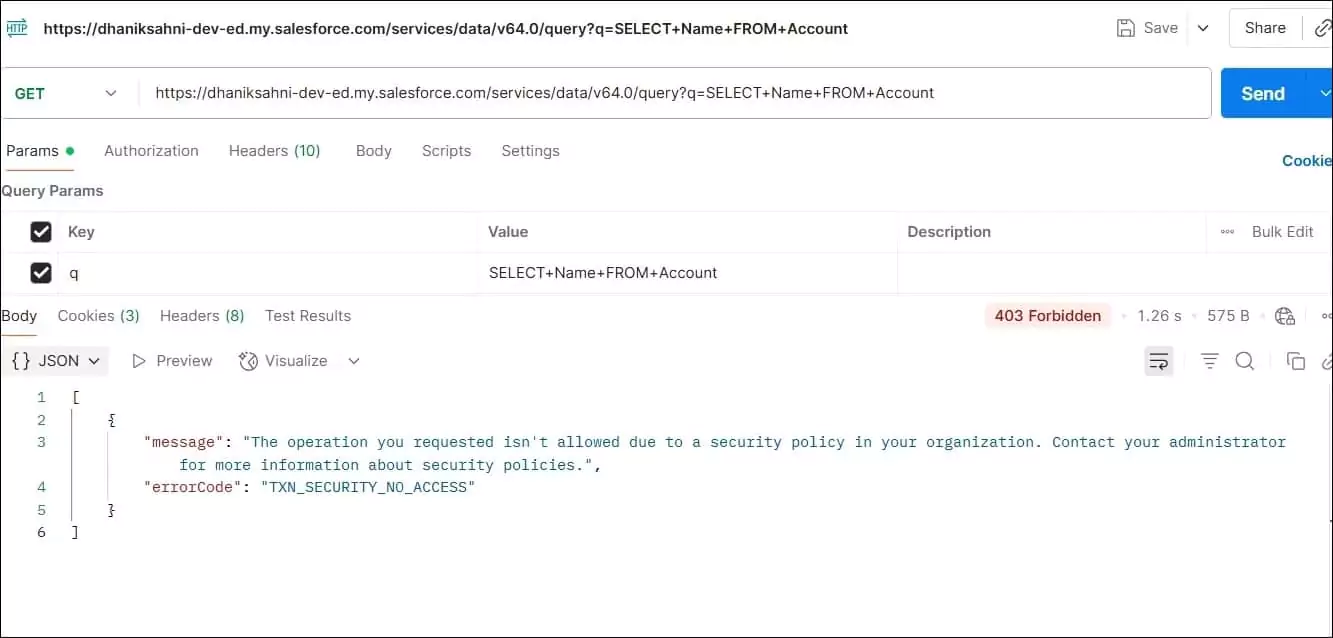
Test in Postman
When data is retrieved using Postman from the Salesforce API, it will block the request and throw an error if more than the agreed limit of records is retrieved.
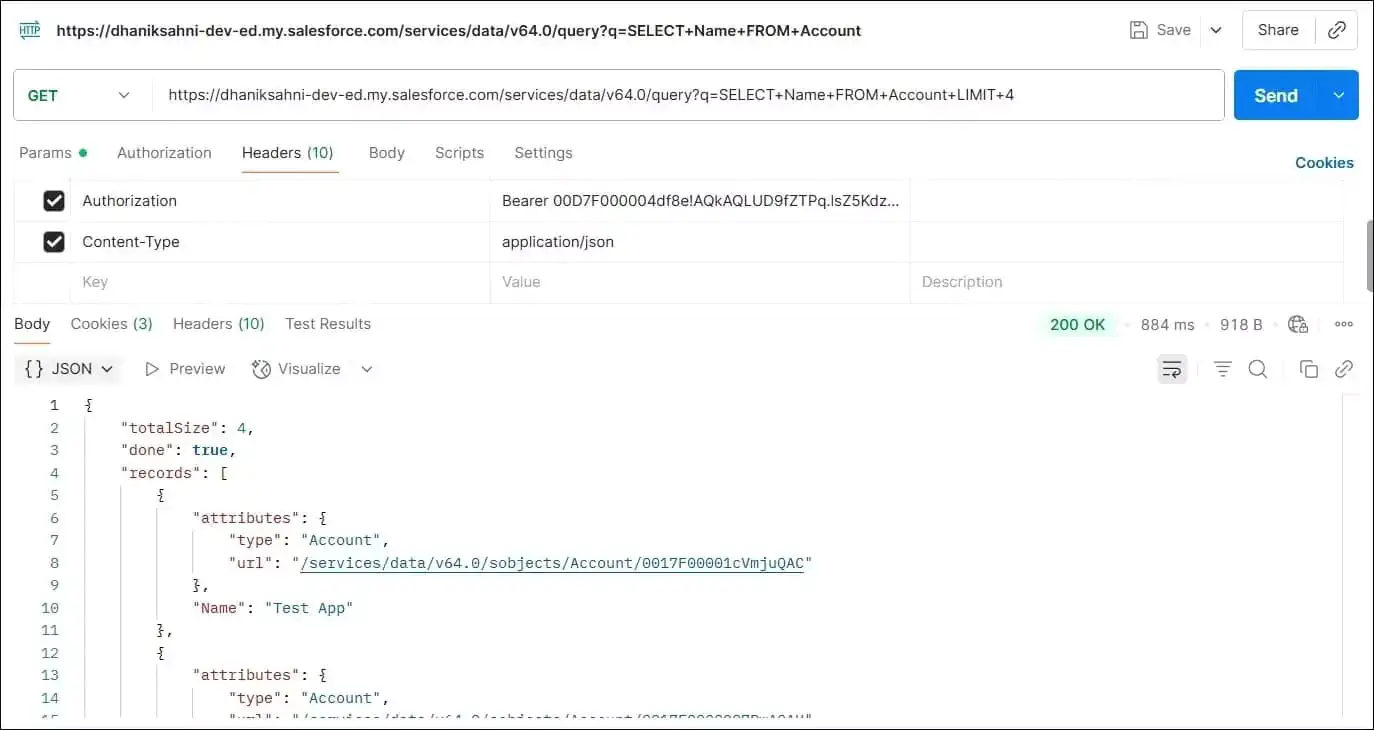
If the record is retrieved within the limit, then we will get a result.
Method 2: Using Apex
We can also implement a similar feature using Apex. The code below will throw the same kind of error. We can use Apex when we need more control over security policy, like when, based on profile, client, or role, we want to enable transaction security.
After the apex class is created, set up the transaction security policy. Select Apex instead of the conditional builder. Use API Event for the event and select the above-created Apex class in the Apex Class drop-down.
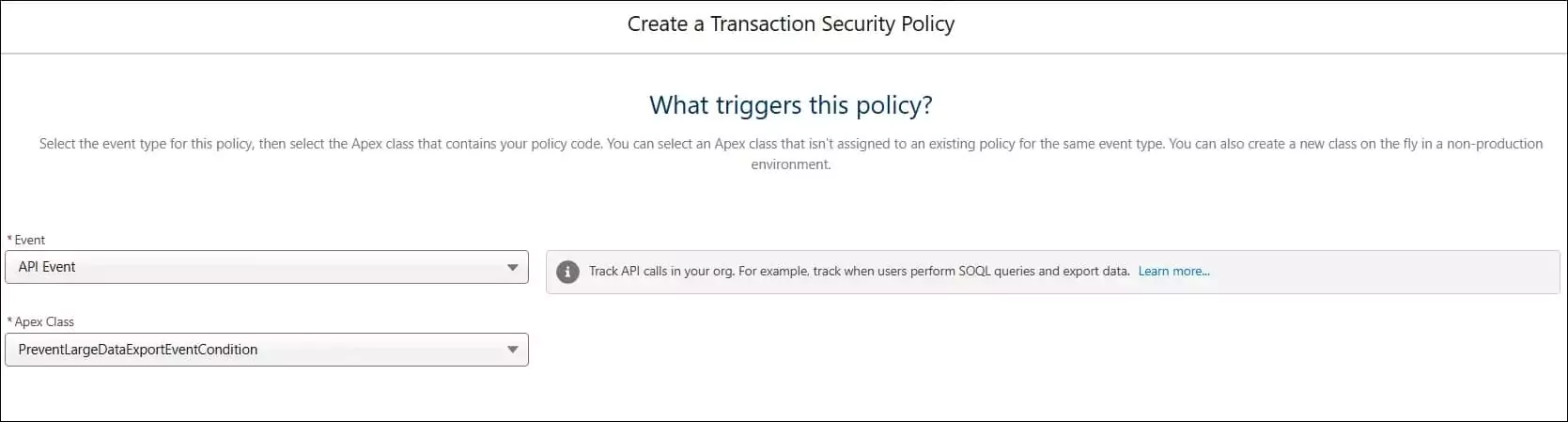
Add event action information to send an alert to admins when a transaction security policy event is triggered

Test in Postman
Data retrieval error will display when complete account data is retrieved.

References
Related Posts
- Top 5 Session Security for LWC
- Salesforce Security Interview Question
- How to Integrate Google reCaptcha v3 into the Salesforce Experience Site
- Streamlining Authentication: Custom Login Flow in Salesforce
- Accessing External Credential Parameters of Named Credential in Salesforce Apex
- Exploring GraphQL API in Salesforce
- Steps for Successful Salesforce data migration
- Secure Apex Code with User Mode Operation
- Salesforce Interview Question for Asynchronous Apex
- Enforce Object-level and Field-level permissions in Apex
- Important facts about Permission Set in Salesforce
Need help with setting up a transaction security policy?
If you need to set up a transaction security policy, contact us.

