Application security is the discipline of processes, tools, and practices aiming to protect applications from threats throughout the entire application lifecycle. We have to properly analyze and handle application security risks. Web developers or administrators should follow best practices while developing applications. This post will explain the basics of securing Salesforce application.
Application security can also help organizations protect all kinds of applications used by internal and external stakeholders including customers, business partners and employees.
Application security issues are growing day by day, in this month only lot of internet fraud and data breach incident happened. See below image to for some reported issues of big organization’s.
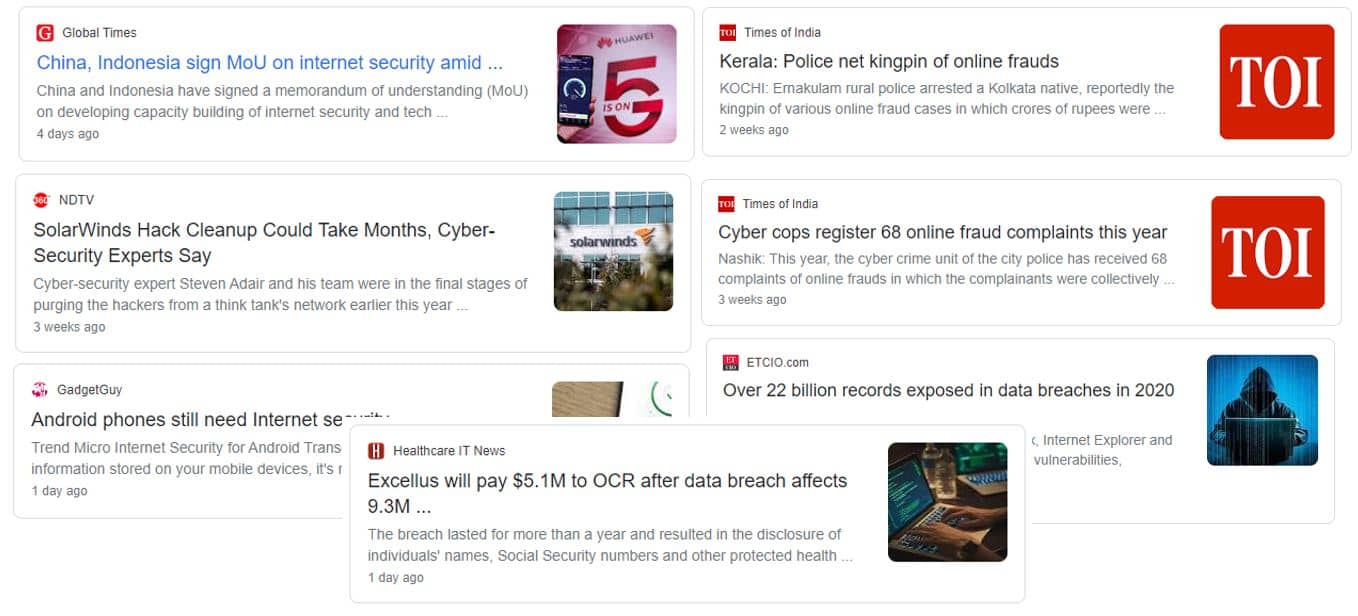
Why should we secure web application?
Internet is nowadays full of security fraud, internet robbery, data breach etc. not only small organization, big organization also facing lot of data security issues. If we see, in this month only lot of internet fraud and data breaches happened.

Based on this internet fraud organizations have to secure their application not from external source but also from internal user. If we are able to make application and our network secure then we can prevents loss of sensitive data. Data is money for business so if we are able to save our data our business reputation and financial loss also can be reduced.
Top Web Application Security Risks
There are many web application flaws where attacker can attack and utilize those to transact into our system or steal our important data. Let us see top web application security risks.
1. Injection:
Injection flaws are when an attacker/hacker uses unfiltered and often malicious data to attack databases or directories connected to web applications.
2. Broken Authentication
Authentication is “broken” when attackers/hackers are able to compromise passwords, keys or session tokens, user account information, and other details to assume user identities.
3. Sensitive Data Exposure
Many APIs and web applications do not properly protect sensitive data, such as financial, healthcare, and PII. Attackers/hackers may steal or modify such weakly protected data to conduct credit card fraud, identity theft, or other crimes.
4. Security Misconfiguration
Security misconfiguration is insecure default configurations, incomplete or ad hoc configurations, open cloud storage, misconfigured HTTP headers, and verbose error messages containing sensitive information. This way attacker can easily login to our system and they can steal data/files.
5. Cross-Site Scripting XSS
Cross-site scripting uses malicious code injected into sites to attack a user’s web browser. An attacker can insert the code through a link and, together with social engineering, will lure the user to clicking the link and executing the code.
6. Cross-Site Request Forgery
Cross-site request forgeries (CSRF) use social engineering to trick authenticated users into clicking a link, as an example and take control of their sessions.
7. Unvalidated Redirects & Forwards
Unvalidated redirects and forwards are possible when a web application accepts untrusted input that could cause the web application to redirect the request to a URL contained within untrusted input.
8. Using Components with Known Vulnerabilities
Many security issues can come with using unfettered code from sources you aren’t familiar with. May be component which we purchased have injection flaw then it will make our application in security risk. So due diligence needs to get done when considering using a third-party code or component in web application.
Is all Salesforce app secure?
We can not say that all Salesforce application is 100% secure. Data security is our priority and we have to initiated proper data governance policy then only our Salesforce app will be secure. As we are creating custom application like customer portal, mobile application or lightning component with untrusted JavaScript libraries, we can be in risk in these cases. So we should write code with best practice and we should use verified trusted libraries only.
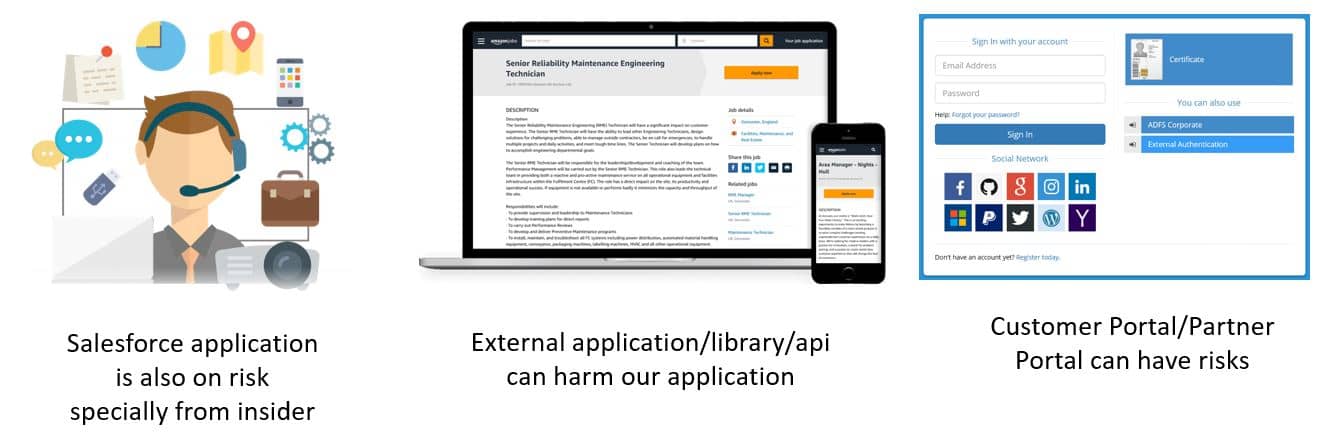
How to secure Salesforce Application?
Salesforce offer two type of security – System level security and Application level security. System level security is implemented for complete Salesforce org like who can access our application and Application level security is mainly controls and restricts what the user can edit, delete and view the values of the field of an Object.
System Level Security:
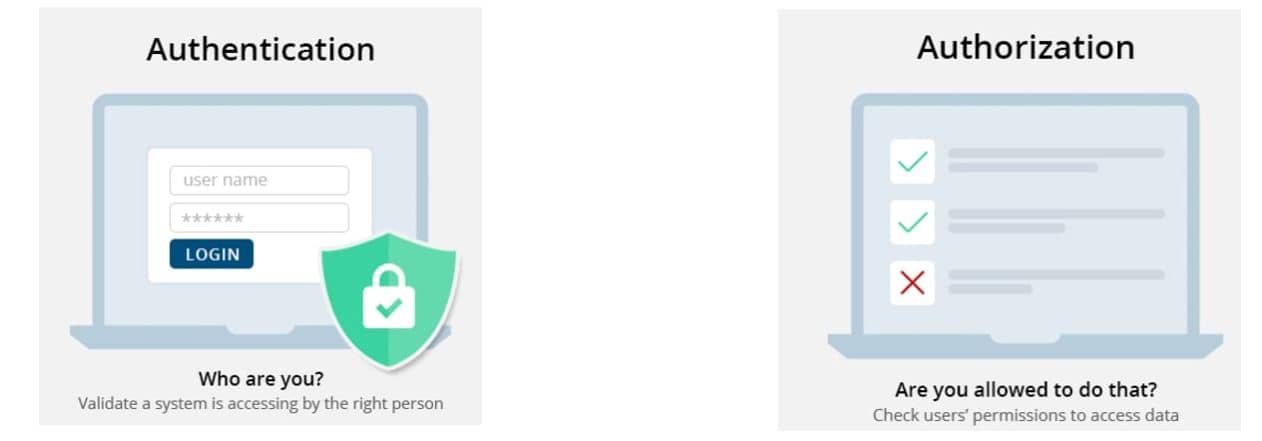
System–level security is a architecture, policy and processes that ensure data and system security on individual or network computer systems. System level security is implemented using authentication and authorization.
Authentication is the process of recognizing a user’s identity. It will prevent unauthorized access to our salesforce org or its data by making sure each logged in user is who they say they are.
Authorization defines which data or features an authenticated user can use. This will be used once authentication is complete and user is into the application. Now what a user can do is implemented using authorization.
Application Level Security:
Application level security controls and restricts what the user can edit, delete and view the values of the field of an Object. Using below implementation we can secure our application.
1. Security Health Check
Use Salesforce Health Check tool to identify and fix potential vulnerabilities in your security settings.
2. Auditing
Auditing provides information about use of the system, which can be critical in diagnosing potential or real security issues. To verify that our Org is actually secure, we should perform audits to monitor for unexpected changes or usage trends.
We can monitor record modification fields, login history for successful and failure attempt, field history tracking and field audit trails.
3. Salesforce Shield
Salesforce Shield is a trio (3 features) of security tools that helps admins and developers build extra levels of trust, compliance, and governance right into business-critical apps.
Shield Platform Encryption:
Shield Platform Encryption allows us to natively encrypt most sensitive data at rest across all your Salesforce apps. Encrypting data at rest adds another layer of protection to PII, sensitive, confidential, or proprietary data. We can add masking as well to more security of PI and PII information.
Real-Time Event Monitoring:
Real-Time Event Monitoring gives you access to detailed performance, security, and usage data on all your Salesforce apps. We can see who is accessing critical business data when, and from where.
Field Audit Trail:
Field Audit Trail lets you know the state and value of your data for any date, at any time. We can use it for regulatory compliance, internal governance, audit, or customer service.
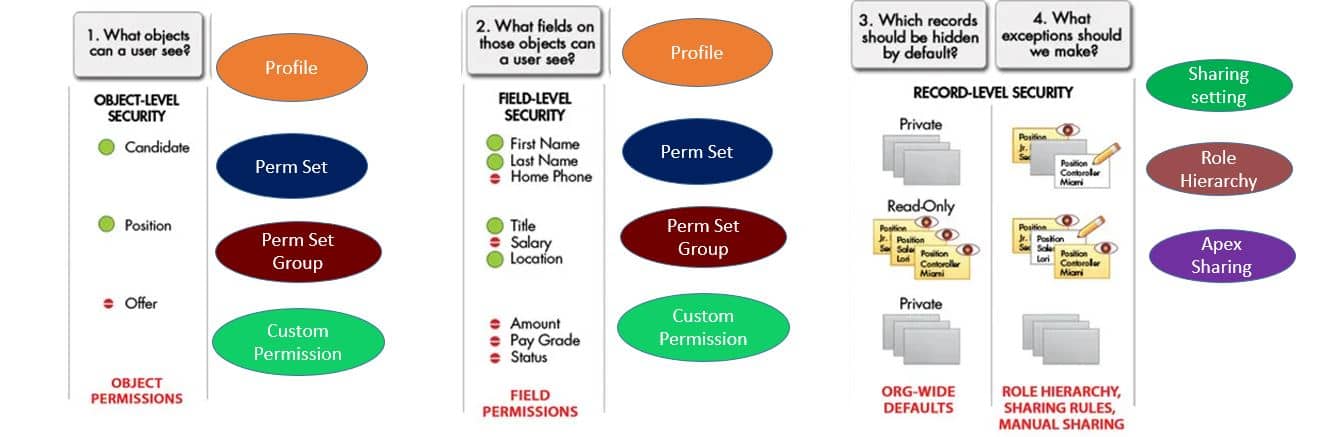
4. Data Security
Using this security feature, we can control which users approach which information in your entire organization, a particular object, a particular field, or an individual record. We can utilize profile, permission set, custom permission, sharing setting, apex sharing, role hierarchy to restrict object and fields and share records.
5. Security Testing
We should get tested our custom code components thoroughly. All permission of object, fields, records should be tested for each profile/permission sets. Customer Portal/Mobile application needs special attention as these will be used by external users.
Session Video:
Reference:
https://trailhead.salesforce.com/content/learn/modules/data_security/data_security_overview


2 Comments
Pingback: What is Salesforce Administrator Job Profile? - SalesforceCodex
Pingback: Difference Between With and Without Security in Apex